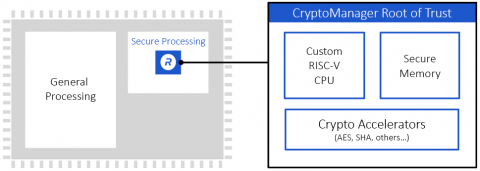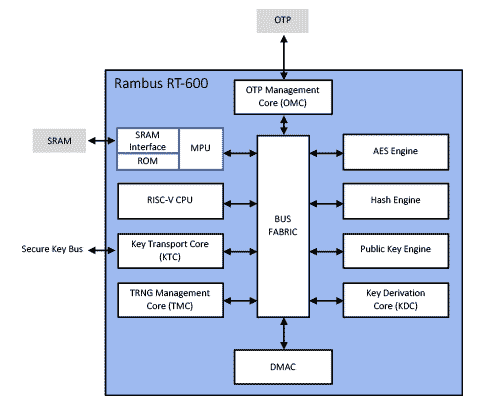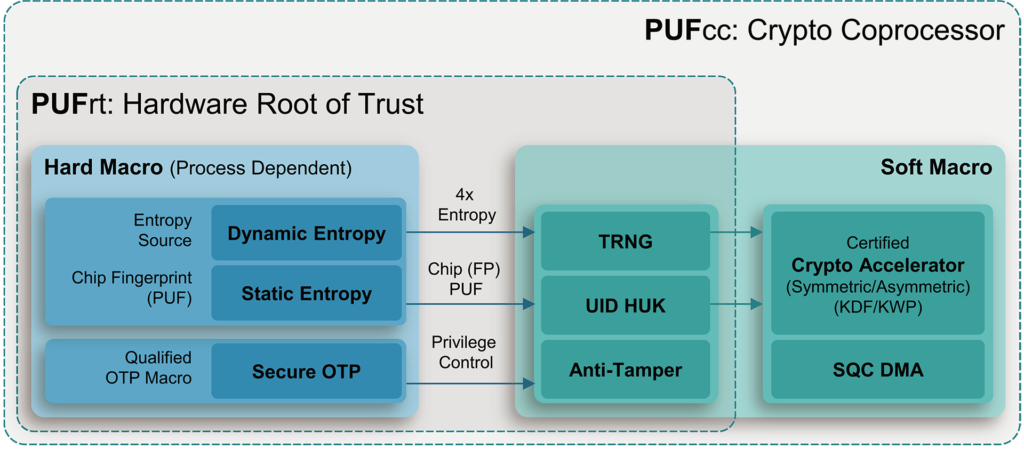
Rambus CryptoManager Root of Trust Cores Certified ASIL-B/D Ready for Enhanced Security in Automotive Applications - Rambus

Is it possible to always identify the actual root cause behind a security incident? | Tales from a Security Professional