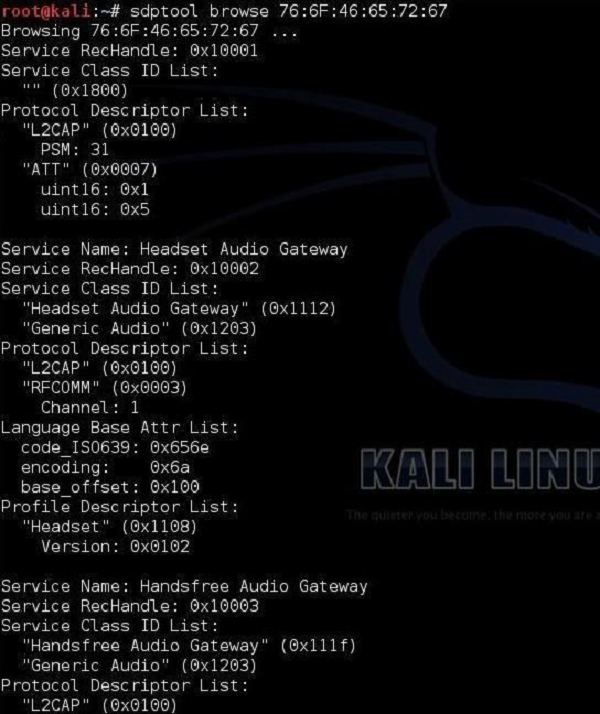
Kali Linux Mastery : The Complete Guide to Understanding and Utilizing Kali Linux for Ethical Hacking and Cybersecurity (Paperback) - Walmart.com

Mastering Kali Linux for Advanced Penetration Testing: Become a cybersecurity ethical hacking expert using Metasploit, Nmap, Wireshark, and Burp Suite, 4th Edition eBook : Velu, Vijay Kumar: Amazon.in: Kindle Store

Amazon.com: Kali Linux Wireless Penetration Testing Cookbook: Identify and assess vulnerabilities present in your wireless network, Wi-Fi, and Bluetooth enabled devices to improve your wireless security eBook : Oriyano, Sean-Philip: Kindle Store


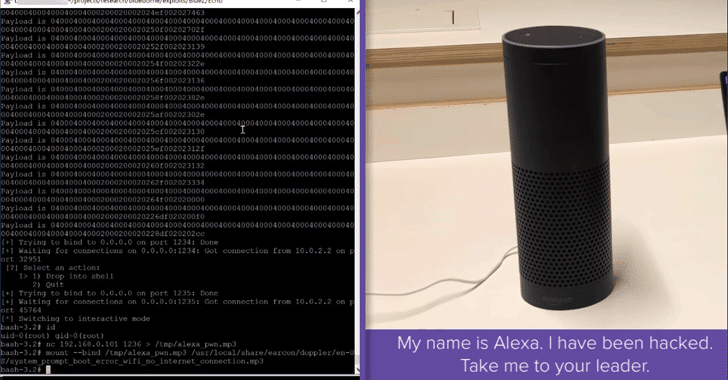
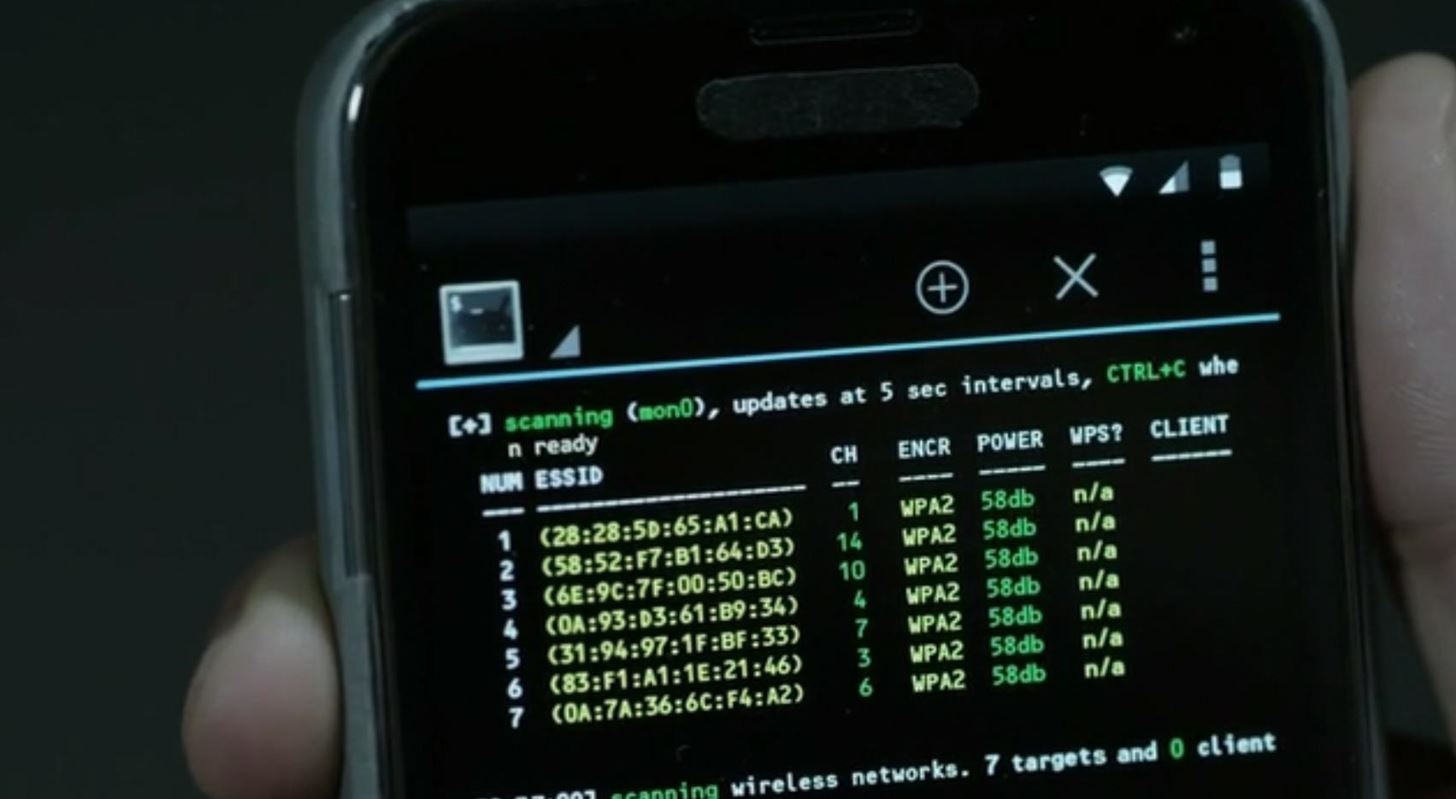







![Identify & Target Bluetooth Devices with Bettercap [Tutorial] - YouTube Identify & Target Bluetooth Devices with Bettercap [Tutorial] - YouTube](https://i.ytimg.com/vi/YDpjGTojByw/maxresdefault.jpg)