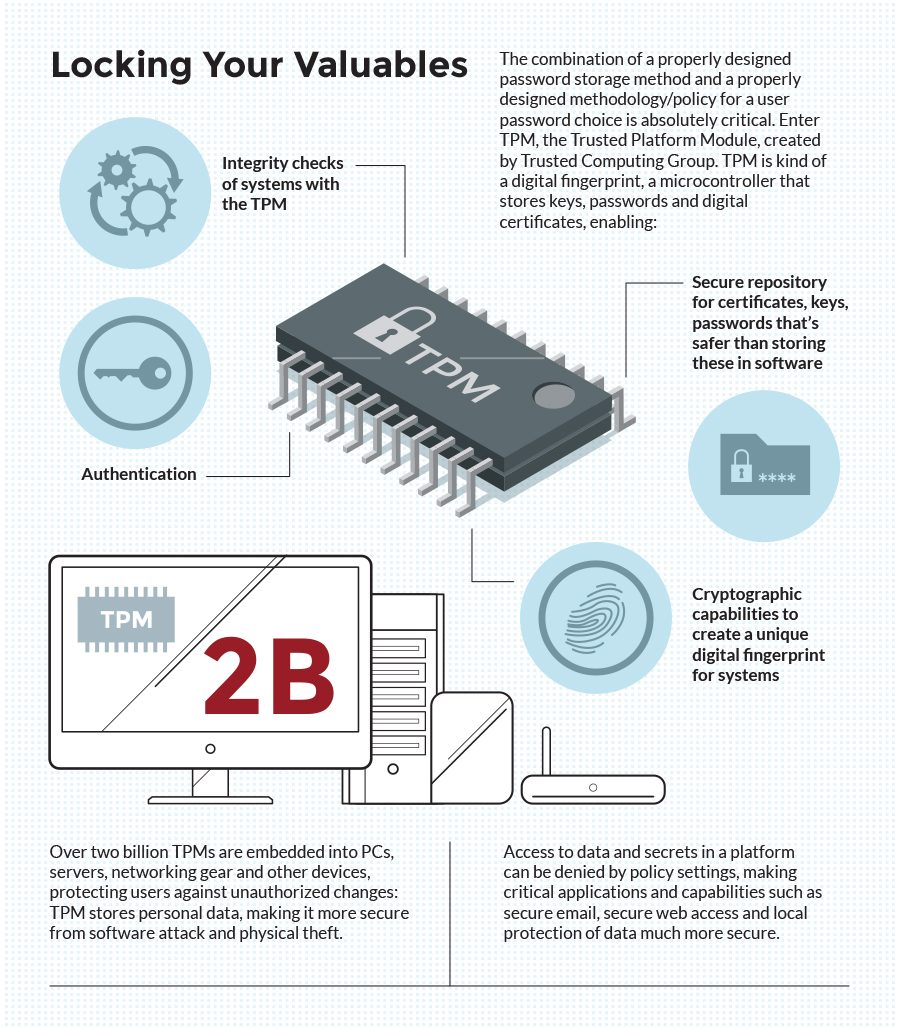
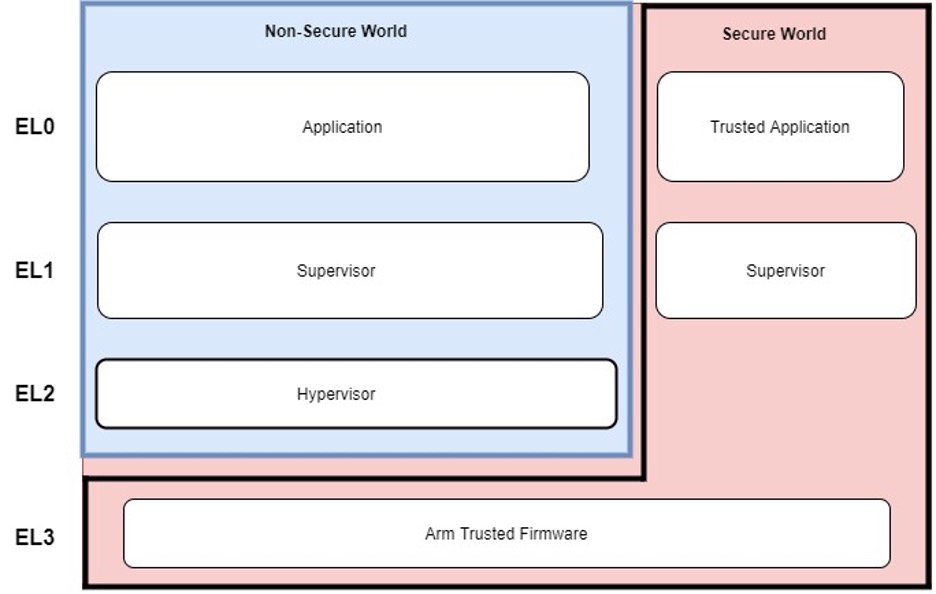
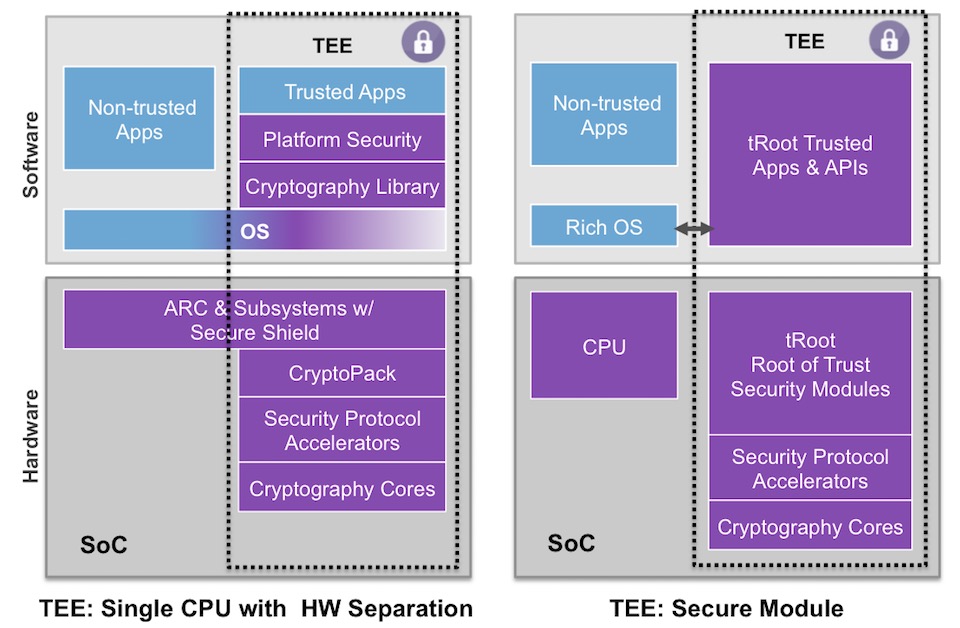
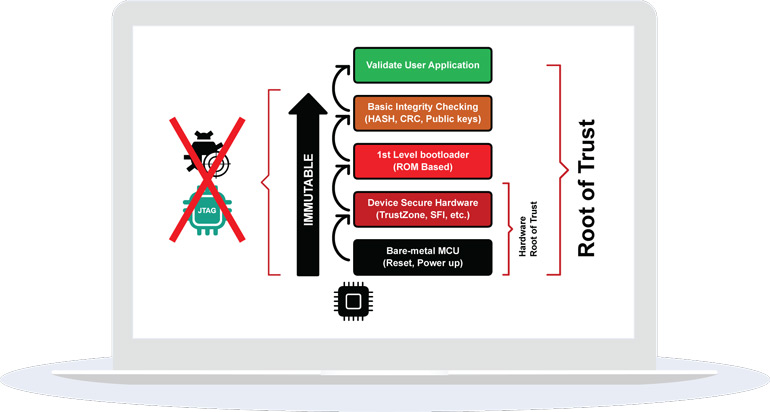
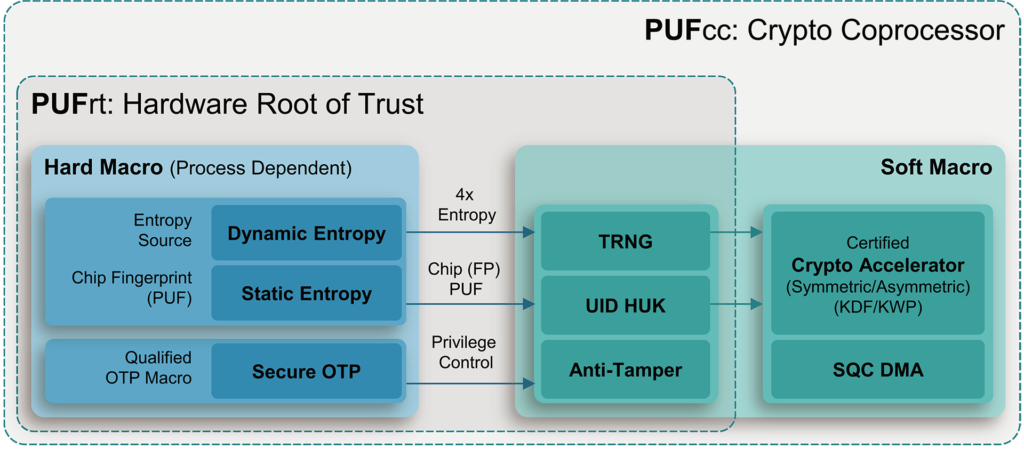
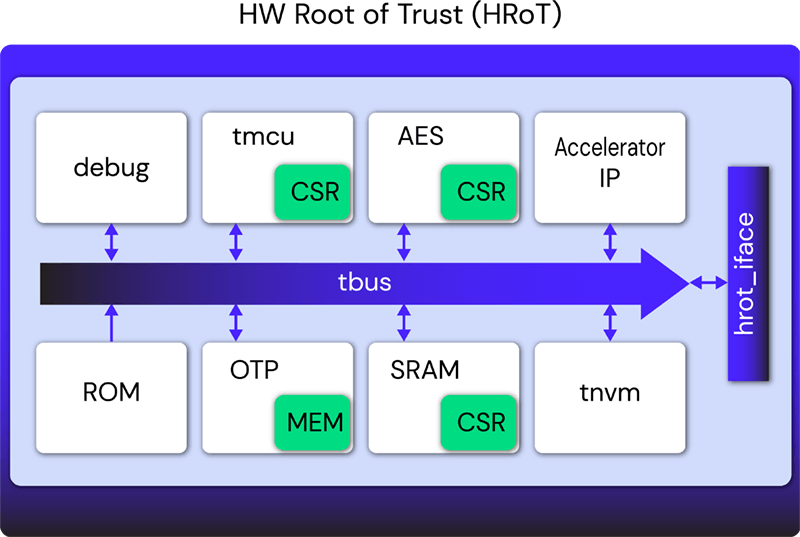
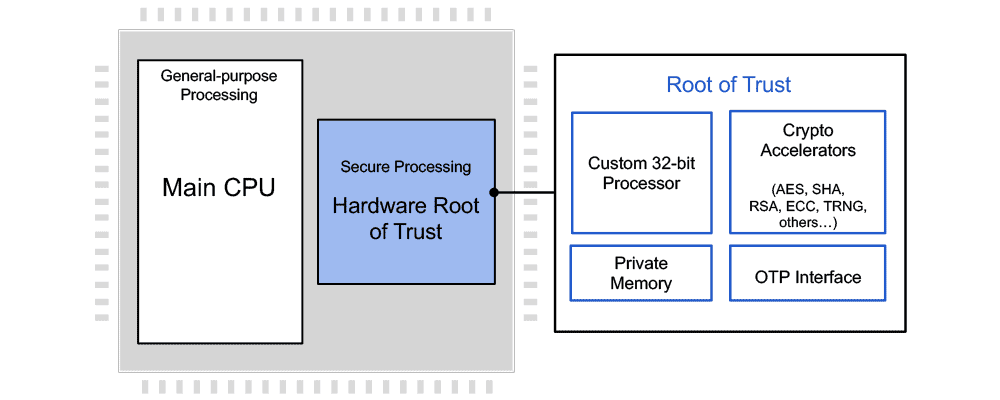
Using a Trusted Platform Module for endpoint device security in AWS IoT Greengrass | The Internet of Things on AWS – Official Blog

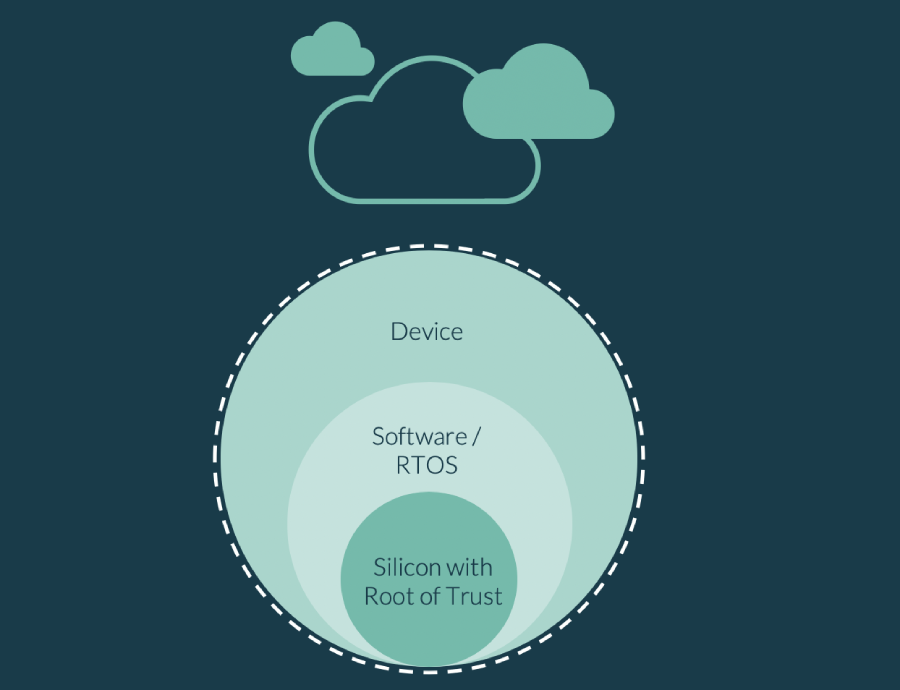
Why HPE Gen10 hardware and its Silicon Root of Trust is a game changer in the server world - BITCON IT consultants